Security Intelligence – Role of Big Data in Fraud Prevention and Management
Fraud is a serious problem and requires new way of thinking to address this problem. Irrespective of the market type whether its financial services, online retail, point of sale or healthcare, fraud prevention and management is the biggest pain point for all customers these days.
In the security market to address Fraud, the real-time security intelligence along with the power of Big Data is spearheading the growth of solution vendors to innovate and differentiate their solutions from old-school security vendors.
Fraud causes companies to lose money in many ways. These days there is a greater need for a real-time solution to help to organizations automatically detect the anomalies with their users or system behaviours early on, which then can help to notify and take appropriate action This will prevent fraud and the loss of revenue.
Let’s take the example of healthcare to list out some of the well know challenges around fraud.
- Organized groups defrauding insurance companies through elaborate schemes against government-sponsored programs or private health insurers
- Patient medical IDs are stolen or duplicated for financial benefits
- User impersonation for prescription drug benefits and many more…
Meanwhile, hospitals and HMO pay a heavy price through fines and litigations if they don’t comply to all the Healthcare laws that are enforced by the government. So, they have to ensure appropriate checks and measures to prevent violations by their users/patients/doctors when they use the applications and systems.
Old school way of Fraud management:
Most companies have invested and adopted multi-factor authentication methods (ex: password, smart cards, One-Time Password (OTP), biometrics etc) as an only mechanism to identify and protect their users who are using their applications and systems but also a way to manage fraud. The picture here suggests a mechanism that they enforce currently to do a fraud evaluation.
These companies have quickly understood that multi-factor authentication alone cannot scale and address fraud issues since the bad guys have figured out a way to break through these multi-factor authentication mechanisms.
This is why there is a need for real-time intelligence security solution!.
Real-time Security Intelligence through Big Data
The challenges that makes realtime intelligence gathering the right approach to address fraud are:
- No single layer or a multi factor authentication is enough to keep determined fraudsters out of enterprise systems. Multiple layers must be employed to defend against today’s attacks and those that are yet to appear.
- No authentication measure on its own, especially when communicating through a browser, is sufficient to counter today’s threats. Additional fraud prevention layers must be utilized.
- Malware is the biggest immediate threat, malware-based attacks are spreading to multiple sectors and enterprises.
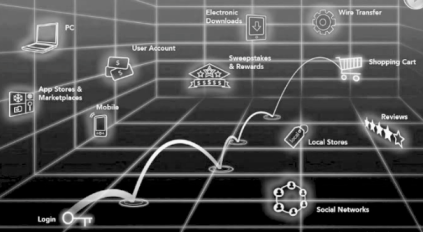 Let’s take the example of an online retail scenario where users have to shop for good through the browser supported on the PC, smart phone or the tablet.
Let’s take the example of an online retail scenario where users have to shop for good through the browser supported on the PC, smart phone or the tablet.
Like the picture shows, a typical user will make multiple clicks and will interact with multiple applications in the background through a browser before he gets to the shopping cart. This would mean there is a way for us to gather a lot more data and information about the user and analyse his behavior realtime
Here are come of the steps that will help us build real-time intelligence around the user behavior:
1. End point Data : involves capturing context of users at the endpoint which is his device. For example is he using the browser on a PC, desktop, tablet, smart phone. Capture the user’s IP, geo-location, authentication credentials and many more.
2. Session Data: gather, monitor and analyze user’s session (ex. http post parameters and other session attributes) and his navigation behavior on the browser. Compare this with his earlier navigation patterns to identify abnormal patterns based on his transitional history.
3. User Data: gather to monitor and analyzes user’s behavior to identify any anomalous behaviors during the transaction .
4. Context Analysis: Analyse the relationships among internal and/or external entities, systems and their attributes (for example, users, accounts, account attributes, machines and machine attributes etc.). Analyze the application logs, system logs, database logs and build predictive models for the user behaviour around applications and the systems involved.
The intelligence gathering and analysis in the above steps involves gathering the right data and also analyzing the data with an effective algorithm. This is where the Big Data plays a role to help build an effective and accurate model based on the user’s interaction with the application and system, that will help detect anomalies and prevent and manage fraud efficiently.
The secret to the success of such a Real-time Security Intelligence solution boils down to the quality of data collection and the advanced algorithms that addresses the 3 Vs of Big Data not only to build accurate predictive models but also support self learning for the solution to get smarter over time.
Posted on January 8, 2013, in Big Data, Blog, IAM, Market Trends. Bookmark the permalink. Leave a comment.


Leave a comment
Comments 0